Hello Fernandez,
Thank you for taking the time to respond.
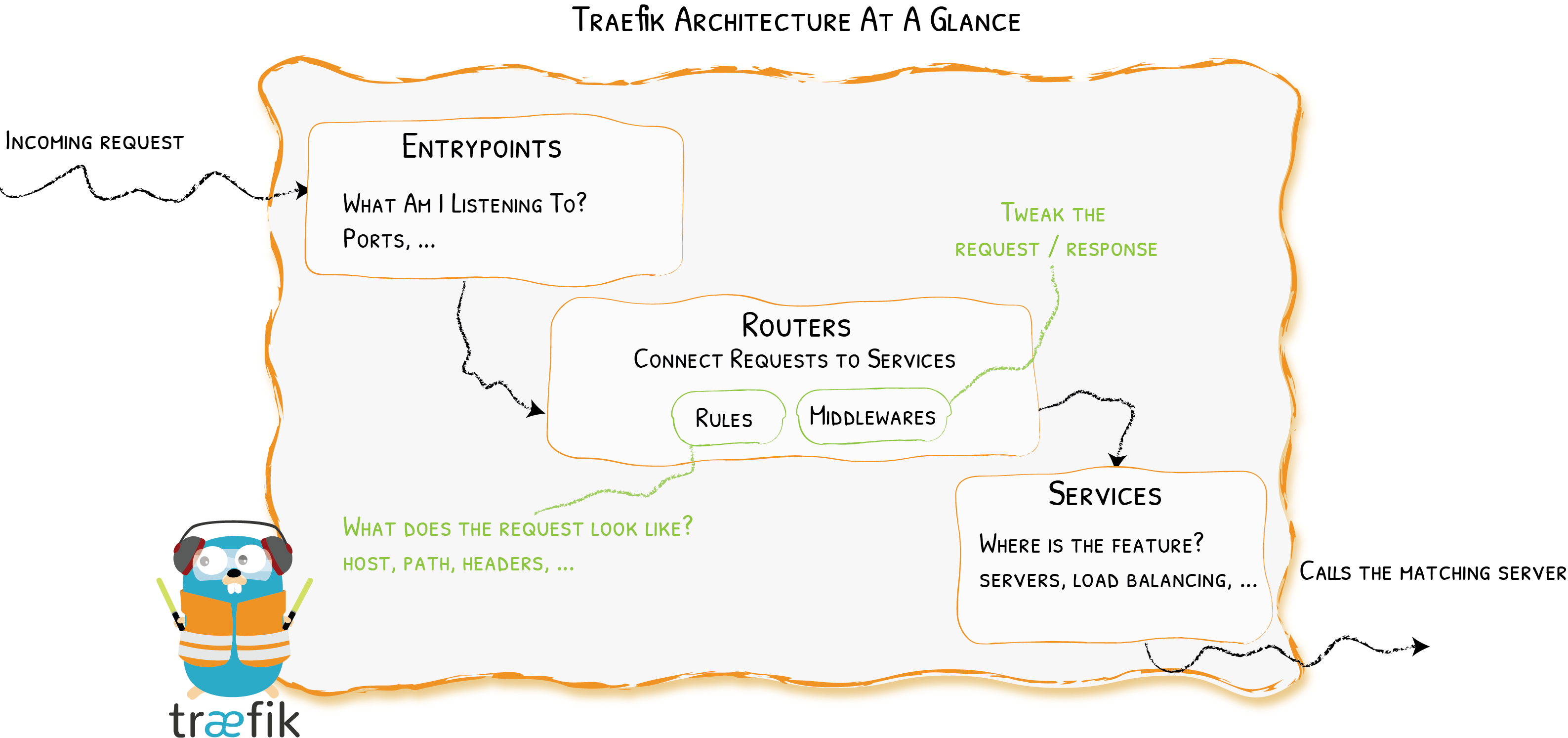
Actually, I mean "entrypoint" in the precise meaning of the diagram and the documentation. The idea is to setup a traefik configuration with 2 endpoints, one endpoint uses a forwardAuth middleware to authenticate a request based on headers, and then forwards the request to a second endpoint, listening ona different port, which will then apply a different routing rule based on the headers returned by the forwardAuth middleware. The second endpoint is not accessible remotely, and only used to apply a second set of routing rules.
I've built a test configuration that has 2 endpoints:
- The first endpoint is on port 80, and applies a forwardAuth middleware and then forwards the request to localhost:10000
- The second endpoint listens on port 10000, and currently only route to a whoami container. The eventual goal is to have it use the docker dynamic provider and route based on the X-Forwarded-User header
The problem is that the routing to the second entrypoint doesn't seem to be working. I can reach the second endpoint if I point a browser at port 10000, but when I go to port 80, the forwardAuth gets applied, and then the logs show that it is being forwarded to localhost:10000. However it looks like the router1 rules on the 'authenticated' endpoint are not finding a match and returns a 404 error.
static config
entryPoints:
authenticated:
address: "127.0.0.1:10000"
web:
address: "127.0.0.1:80"
http:
routers:
router0:
service: whoami
rule: "Host(\"localhost\")"
entryPoints: ['web']
middlewares:
- authsvc
router1:
service: whoami2
entryPoints: ['authenticated']
rule: "Host(\"localhost\")"
middlewares:
authsvc:
forwardAuth:
trustForwardHeader: true
authResponseHeaders:
- X-Forwarded-User
address: "http://authsvc/"
services:
whoami:
loadBalancer:
servers:
- url: "http://127.0.0.1:10000/"
whoami2:
loadBalancer:
servers:
- url: "http://whoami2/"
First curl command against the 'web' endpoint and log entries
curl -vv -b kbase_session=DELETED http://localhost/
* Trying ::1...
* TCP_NODELAY set
* Connected to localhost (::1) port 80 (#0)
> GET / HTTP/1.1
> Host: localhost
> User-Agent: curl/7.54.0
> Accept: */*
> Cookie: kbase_session=DELETED
>
< HTTP/1.1 404 Not Found
< Content-Length: 19
< Content-Type: text/plain; charset=utf-8
< Date: Thu, 26 Sep 2019 16:34:25 GMT
< X-Content-Type-Options: nosniff
<
404 page not found
* Connection #0 to host localhost left intact
[log entries for this request]
authsvc_1 | ('Got a request with cookie ', DELETED')
authsvc_1 | [pid: 8|app: 0|req: 1/1] 172.30.0.4 () {52 vars in 667 bytes} [Thu Sep 26 16:34:22 2019] GET / => generated 2 bytes in 3263 msecs (HTTP/1.1 200) 3 headers in 104 bytes (1 switches on core 0)
traefik | time="2019-09-26T16:34:25Z" level=debug msg="vulcand/oxy/roundrobin/rr: begin ServeHttp on request" Request="{\"Method\":\"GET\",\"URL\":{\"Scheme\":\"\",\"Opaque\":\"\",\"User\":null,\"Host\":\"\",\"Path\":\"/\",\"RawPath\":\"\",\"ForceQuery\":false,\"RawQuery\":\"\",\"Fragment\":\"\"},\"Proto\":\"HTTP/1.1\",\"ProtoMajor\":1,\"ProtoMinor\":1,\"Header\":{\"Accept\":[\"*/*\"],\"Cookie\":[\"kbase_session=DELETED\"],\"User-Agent\":[\"curl/7.54.0\"],\"X-Forwarded-Host\":[\"localhost\"],\"X-Forwarded-Port\":[\"80\"],\"X-Forwarded-Proto\":[\"http\"],\"X-Forwarded-Server\":[\"fcc6ba3f19f1\"],\"X-Forwarded-User\":[\"sychan\"],\"X-Real-Ip\":[\"172.30.0.1\"]},\"ContentLength\":0,\"TransferEncoding\":null,\"Host\":\"localhost\",\"Form\":null,\"PostForm\":null,\"MultipartForm\":null,\"Trailer\":null,\"RemoteAddr\":\"172.30.0.1:35252\",\"RequestURI\":\"/\",\"TLS\":null}"
traefik | time="2019-09-26T16:34:25Z" level=debug msg="vulcand/oxy/roundrobin/rr: Forwarding this request to URL" Request="{\"Method\":\"GET\",\"URL\":{\"Scheme\":\"\",\"Opaque\":\"\",\"User\":null,\"Host\":\"\",\"Path\":\"/\",\"RawPath\":\"\",\"ForceQuery\":false,\"RawQuery\":\"\",\"Fragment\":\"\"},\"Proto\":\"HTTP/1.1\",\"ProtoMajor\":1,\"ProtoMinor\":1,\"Header\":{\"Accept\":[\"*/*\"],\"Cookie\":[\"kbase_session=DELETED\"],\"User-Agent\":[\"curl/7.54.0\"],\"X-Forwarded-Host\":[\"localhost\"],\"X-Forwarded-Port\":[\"80\"],\"X-Forwarded-Proto\":[\"http\"],\"X-Forwarded-Server\":[\"fcc6ba3f19f1\"],\"X-Forwarded-User\":[\"sychan\"],\"X-Real-Ip\":[\"172.30.0.1\"]},\"ContentLength\":0,\"TransferEncoding\":null,\"Host\":\"localhost\",\"Form\":null,\"PostForm\":null,\"MultipartForm\":null,\"Trailer\":null,\"RemoteAddr\":\"172.30.0.1:35252\",\"RequestURI\":\"/\",\"TLS\":null}" ForwardURL="http://127.0.0.1:10000/"
traefik | time="2019-09-26T16:34:25Z" level=debug msg="vulcand/oxy/roundrobin/rr: completed ServeHttp on request" Request="{\"Method\":\"GET\",\"URL\":{\"Scheme\":\"\",\"Opaque\":\"\",\"User\":null,\"Host\":\"\",\"Path\":\"/\",\"RawPath\":\"\",\"ForceQuery\":false,\"RawQuery\":\"\",\"Fragment\":\"\"},\"Proto\":\"HTTP/1.1\",\"ProtoMajor\":1,\"ProtoMinor\":1,\"Header\":{\"Accept\":[\"*/*\"],\"Cookie\":[\"kbase_session=DELETED\"],\"User-Agent\":[\"curl/7.54.0\"],\"X-Forwarded-Host\":[\"localhost\"],\"X-Forwarded-Port\":[\"80\"],\"X-Forwarded-Proto\":[\"http\"],\"X-Forwarded-Server\":[\"fcc6ba3f19f1\"],\"X-Forwarded-User\":[\"sychan\"],\"X-Real-Ip\":[\"172.30.0.1\"]},\"ContentLength\":0,\"TransferEncoding\":null,\"Host\":\"localhost\",\"Form\":null,\"PostForm\":null,\"MultipartForm\":null,\"Trailer\":null,\"RemoteAddr\":\"172.30.0.1:35252\",\"RequestURI\":\"/\",\"TLS\":null}"
Here is a curl command to the second endpoint, that just routes to whoami (for now)
curl -vv http://localhost:10000/
* Trying ::1...
* TCP_NODELAY set
* Connected to localhost (::1) port 10000 (#0)
> GET / HTTP/1.1
> Host: localhost:10000
> User-Agent: curl/7.54.0
> Accept: */*
>
< HTTP/1.1 200 OK
< Content-Length: 341
< Content-Type: text/plain; charset=utf-8
< Date: Thu, 26 Sep 2019 16:35:58 GMT
<
Hostname: whoami2
IP: 127.0.0.1
IP: 172.30.0.5
RemoteAddr: 172.30.0.4:48152
GET / HTTP/1.1
Host: whoami2
User-Agent: curl/7.54.0
Accept: */*
Accept-Encoding: gzip
X-Forwarded-For: 172.30.0.1
X-Forwarded-Host: localhost:10000
X-Forwarded-Port: 10000
X-Forwarded-Proto: http
X-Forwarded-Server: fcc6ba3f19f1
X-Real-Ip: 172.30.0.1
* Connection #0 to host localhost left intact
[log entries for this request]
traefik | time="2019-09-26T16:35:58Z" level=debug msg="vulcand/oxy/roundrobin/rr: begin ServeHttp on request" Request="{\"Method\":\"GET\",\"URL\":{\"Scheme\":\"\",\"Opaque\":\"\",\"User\":null,\"Host\":\"\",\"Path\":\"/\",\"RawPath\":\"\",\"ForceQuery\":false,\"RawQuery\":\"\",\"Fragment\":\"\"},\"Proto\":\"HTTP/1.1\",\"ProtoMajor\":1,\"ProtoMinor\":1,\"Header\":{\"Accept\":[\"*/*\"],\"User-Agent\":[\"curl/7.54.0\"],\"X-Forwarded-Host\":[\"localhost:10000\"],\"X-Forwarded-Port\":[\"10000\"],\"X-Forwarded-Proto\":[\"http\"],\"X-Forwarded-Server\":[\"fcc6ba3f19f1\"],\"X-Real-Ip\":[\"172.30.0.1\"]},\"ContentLength\":0,\"TransferEncoding\":null,\"Host\":\"localhost:10000\",\"Form\":null,\"PostForm\":null,\"MultipartForm\":null,\"Trailer\":null,\"RemoteAddr\":\"172.30.0.1:56428\",\"RequestURI\":\"/\",\"TLS\":null}"
traefik | time="2019-09-26T16:35:58Z" level=debug msg="vulcand/oxy/roundrobin/rr: Forwarding this request to URL" Request="{\"Method\":\"GET\",\"URL\":{\"Scheme\":\"\",\"Opaque\":\"\",\"User\":null,\"Host\":\"\",\"Path\":\"/\",\"RawPath\":\"\",\"ForceQuery\":false,\"RawQuery\":\"\",\"Fragment\":\"\"},\"Proto\":\"HTTP/1.1\",\"ProtoMajor\":1,\"ProtoMinor\":1,\"Header\":{\"Accept\":[\"*/*\"],\"User-Agent\":[\"curl/7.54.0\"],\"X-Forwarded-Host\":[\"localhost:10000\"],\"X-Forwarded-Port\":[\"10000\"],\"X-Forwarded-Proto\":[\"http\"],\"X-Forwarded-Server\":[\"fcc6ba3f19f1\"],\"X-Real-Ip\":[\"172.30.0.1\"]},\"ContentLength\":0,\"TransferEncoding\":null,\"Host\":\"localhost:10000\",\"Form\":null,\"PostForm\":null,\"MultipartForm\":null,\"Trailer\":null,\"RemoteAddr\":\"172.30.0.1:56428\",\"RequestURI\":\"/\",\"TLS\":null}" ForwardURL="http://whoami2/"
traefik | time="2019-09-26T16:35:58Z" level=debug msg="vulcand/oxy/roundrobin/rr: completed ServeHttp on request" Request="{\"Method\":\"GET\",\"URL\":{\"Scheme\":\"\",\"Opaque\":\"\",\"User\":null,\"Host\":\"\",\"Path\":\"/\",\"RawPath\":\"\",\"ForceQuery\":false,\"RawQuery\":\"\",\"Fragment\":\"\"},\"Proto\":\"HTTP/1.1\",\"ProtoMajor\":1,\"ProtoMinor\":1,\"Header\":{\"Accept\":[\"*/*\"],\"User-Agent\":[\"curl/7.54.0\"],\"X-Forwarded-Host\":[\"localhost:10000\"],\"X-Forwarded-Port\":[\"10000\"],\"X-Forwarded-Proto\":[\"http\"],\"X-Forwarded-Server\":[\"fcc6ba3f19f1\"],\"X-Real-Ip\":[\"172.30.0.1\"]},\"ContentLength\":0,\"TransferEncoding\":null,\"Host\":\"localhost:10000\",\"Form\":null,\"PostForm\":null,\"MultipartForm\":null,\"Trailer\":null,\"RemoteAddr\":\"172.30.0.1:56428\",\"RequestURI\":\"/\",\"TLS\":null}"
It looks like the router2 rules fail to match because the original port that it came in on was port 80, and not port 10000? Any ideas how I can get the forwarding to work and have the rules for endpoint "authenticated" match the request?