I've been having issues with Traefik issuing Let's Encrypt certs and I can't seem to find the solution to them.
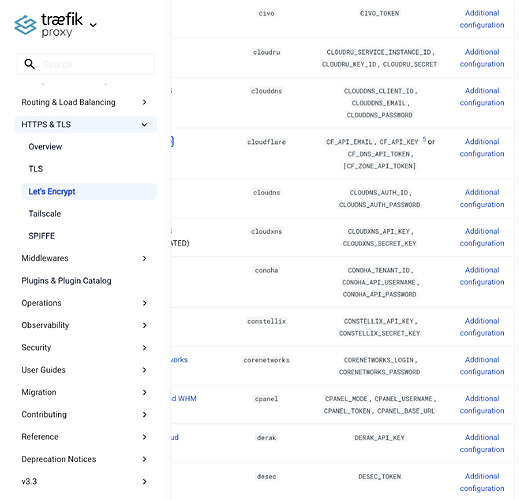
I had previously successfully gotten it to work, but since a few weeks I've been getting errors with the variable naming for cloudflare tokens. The latest documentation calls for CF_DNS_API_TOKEN and CF_API_EMAIL, but the logs are showing errors saying that "CLOUDFLARE_EMAIL,CLOUDFLARE_API_KEY" or "CLOUDFLARE_DNS_API_TOKEN,CLOUDFLARE_ZONE_API_TOKEN" are missing.
Here is the folder tree:
$ tree -pau
[drwxr-xr-x user ] .
|-- [-rw------- user ] .env
|-- [drwxr-xr-x user ] data
| |-- [-rw------- user ] .htpasswd
| |-- [-rw------- root ] acme.json
| `-- [drwxr-xr-x user ] dynamic
| `-- [-rw-r--r-- user ] dynamic-pihole.yml
`-- [-rw-r--r-- user ] docker-compose.yml
My compose file:
services:
traefik:
image: "traefik:3.3"
hostname: '{{.Node.Hostname}}'
ports:
- target: 80
published: 80
protocol: tcp
mode: host
- target: 443
published: 443
protocol: tcp
mode: host
networks:
- traefik_net
volumes:
- "/var/run/docker.sock:/var/run/docker.sock"
- "/home/user/docker/traefik/data:/etc/traefik"
- "/home/user/docker/traefik/data/dynamic:/etc/traefik/dynamic:ro"
command:
# API & Dashboard
- "--api=true"
- "--api.dashboard=true"
- "--log.level=DEBUG"
# Providers
- "--providers.swarm=true"
- "--providers.swarm.exposedByDefault=false"
- "--providers.swarm.network=traefik_net"
- "--providers.file.directory=/etc/traefik/dynamic"
- "--providers.file.watch=true"
# Entrypoints
- "--entrypoints.web.address=:80"
- "--entrypoints.web.http.redirections.entrypoint.to=websecure"
- "--entrypoints.web.http.redirections.entrypoint.scheme=https"
- "--entrypoints.web.http.redirections.entrypoint.permanent=true"
- "--entrypoints.websecure.address=:443"
- "--entrypoints.websecure.asDefault=true"
# Certificate Resolvers
- "--certificatesresolvers.cloudflare.acme.email=${CF_API_EMAIL}"
- "--certificatesresolvers.cloudflare.acme.storage=/etc/traefik/acme.json"
- "--certificatesresolvers.cloudflare.acme.dnschallenge=true"
- "--certificatesresolvers.cloudflare.acme.dnschallenge.provider=cloudflare"
- "--certificatesresolvers.cloudflare.acme.dnschallenge.propagation.delayBeforeChecks=10s"
- "--certificatesresolvers.cloudflare.acme.caserver=https://acme-staging-v02.api.letsencrypt.org/directory"
environment:
- CF_DNS_API_TOKEN=${CF_DNS_API_TOKEN}
- CF_API_EMAIL=${CF_API_EMAIL}
- CF_ZONE_API_TOKEN=${CF_DNS_API_TOKEN}
#- CLOUDFLARE_DNS_API_TOKEN=${CF_DNS_API_TOKEN}
#- CLOUDFLARE_EMAIL=${CF_API_EMAIL}
- TZ=Europe/Nicosia
deploy:
placement:
constraints:
- node.hostname == ubuntu01
restart_policy:
condition: on-failure
delay: 10s
max_attempts: 3
window: 300s
labels:
- "traefik.enable=true"
# Dashboard router:
- "traefik.http.routers.traefik-dashboard.rule=Host(`traefik.my.domain`)"
- "traefik.http.routers.traefik-dashboard.entrypoints=websecure"
- "traefik.http.routers.traefik-dashboard.service=api@internal"
- "traefik.http.routers.traefik-dashboard.middlewares=admin-auth"
- "traefik.http.routers.traefik-dashboard.tls=true"
- "traefik.http.routers.traefik-dashboard.tls.certresolver=cloudflare"
- "traefik.http.routers.traefik-dashboard.tls.domains[0].main=my.domain"
- "traefik.http.routers.traefik-dashboard.tls.domains[0].sans=*.my.domain"
# Middleware
- "traefik.http.middlewares.admin-auth.basicauth.usersfile=/etc/traefik/.htpasswd"
# Dummy port
- "traefik.http.services.traefik.loadbalancer.server.port=80"
networks:
traefik_net:
name: traefik_net
external: true
What I think are the relevant log lines:
traefik_traefik.1.q0a1tiu3444u@ubuntu01 | 2025-07-17T12:21:18+03:00 DBG github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:270 > Building ACME client... providerName=cloudflare.acme
traefik_traefik.1.q0a1tiu3444u@ubuntu01 | 2025-07-17T12:21:18+03:00 DBG github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:276 > https://acme-staging-v02.api.letsencrypt.org/directory providerName=cloudflare.acme
traefik_traefik.1.q0a1tiu3444u@ubuntu01 | 2025-07-17T12:21:19+03:00 INF github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:457 > Register... providerName=cloudflare.acme
traefik_traefik.1.q0a1tiu3444u@ubuntu01 | 2025-07-17T12:21:19+03:00 DBG github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:317 > Using DNS Challenge provider: cloudflare providerName=cloudflare.acme
traefik_traefik.1.q0a1tiu3444u@ubuntu01 | 2025-07-17T12:21:19+03:00 ERR github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:553 > Unable to obtain ACME certificate for domains error="cannot get ACME client cloudflare: some credentials information are missing: CLOUDFLARE_EMAIL,CLOUDFLARE_API_KEY or some credentials information are missing: CLOUDFLARE_DNS_API_TOKEN,CLOUDFLARE_ZONE_API_TOKEN" ACME CA=https://acme-staging-v02.api.letsencrypt.org/directory acmeCA=https://acme-staging-v02.api.letsencrypt.org/directory domains=["my.domain","*.my.domain"] providerName=cloudflare.acme routerName=traefik-dashboard@swarm rule=Host(`traefik.my.domain`)
It's always those same ones repeated (.../acme/provider.go:270, 276, 457, 317, 553.
What am I missing? Please help!
Thanks!