Hey everyone out there.
Sorry in advance for my very basic question.
As a Noob I try to understand traefik behavior and set up a first example.
I read a lot in the forums and came to a point where some things are working, others not.
Somewhen later I want to run Nextcloud-AIO behind traefik v3 but I feel I’m far away from it still.
I run Docker version 29.0.1, build eedd969 on Ubuntu 24.04
I got the below example working. I conclude from this, that my domain setup is fine, requests are routed to traefik on my server and also the letsencrypt setup is working.
Question a) traefik dashboard is accessible but does only provide default certs, why doesn’t it serve letsencrypt certs? I already renewed acme.json to acquire new certificates, but same behavior.
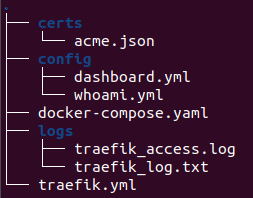
This is my docker-compose.yml:
services:
traefik:
image: traefik:latest
container_name: traefik
restart: unless-stopped
security_opt:
- no-new-privileges:true
environment:
- TZ=Europe/Amsterdam
networks:
# Connect to the 'traefik_proxy' overlay network for inter-container communication across nodes
- proxy
ports:
- "80:80"
- "443:443"
- "8080:8080"
volumes:
- /var/run/docker.sock:/var/run/docker.sock:ro
# - ./traefik.yml:/traefik.yml:ro # Traefik config file
- ./certs:/certs
- ./config:/config:ro # This folder is currently empty
- ./logs:/logs
command:
- "--log.level=DEBUG"
- "--log.filepath=/logs/log.txt"
- "--api.dashboard=true"
- "--api.insecure=false"
- "--providers.docker=true"
- "--providers.docker.exposedbydefault=false"
- "--entryPoints.websecure.address=:443"
- "--certificatesresolvers.myresolver.acme.tlschallenge=true"
# - "--certificatesresolvers.myresolver.acme.caserver=https://acme-staging-v02.api.letsencrypt.org/directory"
- "--certificatesresolvers.myresolver.acme.email=myemailaddr@gmx.com"
- "--certificatesresolvers.myresolver.acme.storage=/certs/acme.json"
# Traefik Dynamic configuration via Docker labels
labels:
# Enable self‑routing
- "traefik.enable=true"
# Dashboard router
- "traefik.http.routers.dashboard.rule=Host(`traefik.mydomain.com`)"
- "traefik.http.routers.dashboard.entrypoints=websecure"
- "traefik.http.routers.dashboard.service=api@internal"
- "traefik.http.routers.dashboard.tls=true"
# Basic-auth middleware
- "traefik.http.middlewares.dashboard-auth.basicauth.users=admin:aHashedPasswd"
- "traefik.http.routers.dashboard.middlewares=dashboard-auth@docker"
# Whoami application
whoami:
image: traefik/whoami
container_name: whoami
restart: unless-stopped
networks:
- proxy
labels:
- "traefik.enable=true"
- "traefik.http.routers.whoami.rule=Host(`whoami.mydomain.com`)"
- "traefik.http.routers.whoami.entrypoints=websecure"
- "traefik.http.routers.whoami.tls=true"
- "traefik.http.routers.whoami.tls.certresolver=myresolver"
- "traefik.http.services.mywhoami.loadbalancer.server.port=80"
networks:
proxy:
name: proxy
I want to run the same example with fileprovider but the following doesn’t work:
docker-compose.yml
services:
traefik:
image: traefik:latest
container_name: traefik
restart: unless-stopped
security_opt:
- no-new-privileges:true
environment:
- TZ=Europe/Amsterdam
networks:
# Connect to the 'traefik_proxy' overlay network for inter-container communication across nodes
proxy:
ports:
- "80:80"
- "443:443"
- "8080:8080"
volumes:
- /var/run/docker.sock:/var/run/docker.sock:ro
- ./traefik.yml:/traefik.yml:ro # Traefik config file
- ./certs:/certs
- ./config:/config:ro
- ./logs:/logs
# Whoami application
whoami:
image: traefik/whoami
container_name: whoami
restart: unless-stopped
networks:
proxy:
networks:
proxy:
name: proxy
traefik.yml:
log:
filePath: "/logs/traefik_log.txt"
format: common
level: debug
accessLog:
format: common
filePath: "logs/traefik_access.log"
api:
dashboard: true # Optional can be disabled
insecure: false # Optional can be disabled
debug: true # Optional can be Enabled if needed for troubleshooting
entryPoints:
web:
address: ":80"
# Optional if you want to redirect all HTTP to HTTPS
http:
redirections:
entryPoint:
to: websecure
scheme: https
websecure:
address: ":443"
#serversTransport:
# insecureSkipVerify: true
providers:
docker:
endpoint: "unix:///var/run/docker.sock"
exposedByDefault: false
network: proxy # Optional; Only use the "proxy" Docker network, even if containers are on multiple networks.
file:
directory: "/config"
watch: true
certificatesResolvers:
letsencrypt:
acme:
email: myemailaddr@gmx.com
storage: /certs/acme.json
caServer: https://acme-v02.api.letsencrypt.org/directory # prod (default)
# caServer: https://acme-staging-v02.api.letsencrypt.org/directory # staging
tlsChallenge: true
http:
routers:
dashboard:
rule: Host(`traefik.mydomain.com`)
service: api@internal
entrypoint: websecure
middlewares:
- auth
middlewares:
auth:
basicAuth:
users:
- "admin:aHashedPasswd"
and ./config/whoami.yml
http:
routers:
whoami:
entrypoints:
- websecure
rule: Host(`whoami.mydomain.com`)
service: whoami@file
tls:
certresolver: letsencrypt
services:
whoami:
loadbalancer:
servers:
port: 80
Interestingly, with this setup I get a valid certificate also for the dashboard at https://traefik.mydomain.com, but the page reports “404 page not found”. Calling up https://whoami.mydomain.com also shows a valid certificate but the message is “internal server error”.
I guess there is some mistake in the config I did not yet understand. I would be very glad if someone could point me to the error.
This is the log file:
2025-11-15T22:22:31+01:00 INF github.com/traefik/traefik/v3/cmd/traefik/traefik.go:167 > Shutting down
2025-11-15T22:47:13+01:00 INF github.com/traefik/traefik/v3/cmd/traefik/traefik.go:108 > Traefik version 3.6.1 built on 2025-11-13T14:16:44Z version=3.6.1
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/cmd/traefik/traefik.go:114 > Static configuration loaded [json] staticConfiguration={"accessLog":{"fields":{"defaultMode":"keep","headers":{"defaultMode":"drop"}},"filePath":"logs/traefik_access.log","filters":{},"format":"common"},"api":{"basePath":"/","dashboard":true,"debug":true},"certificatesResolvers":{"letsencrypt":{"acme":{"caServer":"https://acme-v02.api.letsencrypt.org/directory","certificatesDuration":2160,"clientResponseHeaderTimeout":"30s","clientTimeout":"2m0s","email":"myemailaddr@gmx.com","keyType":"RSA4096","storage":"/certs/acme.json","tlsChallenge":{}}}},"entryPoints":{"web":{"address":":80","forwardedHeaders":{},"http":{"maxHeaderBytes":1048576,"redirections":{"entryPoint":{"permanent":true,"priority":9223372036854775806,"scheme":"https","to":"websecure"}},"sanitizePath":true},"http2":{"maxConcurrentStreams":250,"maxDecoderHeaderTableSize":4096,"maxEncoderHeaderTableSize":4096},"transport":{"lifeCycle":{"graceTimeOut":"10s"},"respondingTimeouts":{"idleTimeout":"3m0s","readTimeout":"1m0s"}},"udp":{"timeout":"3s"}},"websecure":{"address":":443","forwardedHeaders":{},"http":{"maxHeaderBytes":1048576,"sanitizePath":true},"http2":{"maxConcurrentStreams":250,"maxDecoderHeaderTableSize":4096,"maxEncoderHeaderTableSize":4096},"transport":{"lifeCycle":{"graceTimeOut":"10s"},"respondingTimeouts":{"idleTimeout":"3m0s","readTimeout":"1m0s"}},"udp":{"timeout":"3s"}}},"global":{"checkNewVersion":true},"log":{"filePath":"/logs/traefik_log.txt","format":"common","level":"debug"},"providers":{"docker":{"defaultRule":"Host(`{{ normalize .Name }}`)","endpoint":"unix:///var/run/docker.sock","network":"proxy","watch":true},"file":{"directory":"/config","watch":true},"providersThrottleDuration":"2s"},"serversTransport":{"maxIdleConnsPerHost":200},"tcpServersTransport":{"dialKeepAlive":"15s","dialTimeout":"30s"}}
2025-11-15T22:47:13+01:00 INF github.com/traefik/traefik/v3/cmd/traefik/traefik.go:636 >
Stats collection is disabled.
Help us improve Traefik by turning this feature on :)
More details on: https://doc.traefik.io/traefik/contributing/data-collection/
2025-11-15T22:47:13+01:00 INF github.com/traefik/traefik/v3/pkg/server/configurationwatcher.go:73 > Starting provider aggregator *aggregator.ProviderAggregator
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/server/server_entrypoint_tcp.go:237 > Starting TCP Server entryPointName=websecure
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/server/server_entrypoint_tcp.go:237 > Starting TCP Server entryPointName=web
2025-11-15T22:47:13+01:00 INF github.com/traefik/traefik/v3/pkg/provider/aggregator/aggregator.go:219 > Starting provider *file.Provider
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/aggregator/aggregator.go:220 > *file.Provider provider configuration config={"directory":"/config","watch":true}
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/file/file.go:122 > add watcher on: /config
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/file/file.go:122 > add watcher on: /config/whoami.yml
2025-11-15T22:47:13+01:00 INF github.com/traefik/traefik/v3/pkg/provider/aggregator/aggregator.go:219 > Starting provider *traefik.Provider
2025-11-15T22:47:13+01:00 INF github.com/traefik/traefik/v3/pkg/provider/aggregator/aggregator.go:219 > Starting provider *acme.ChallengeTLSALPN
2025-11-15T22:47:13+01:00 INF github.com/traefik/traefik/v3/pkg/provider/aggregator/aggregator.go:219 > Starting provider *docker.Provider
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/aggregator/aggregator.go:220 > *acme.ChallengeTLSALPN provider configuration config={}
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/aggregator/aggregator.go:220 > *traefik.Provider provider configuration config={}
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/aggregator/aggregator.go:220 > *docker.Provider provider configuration config={"defaultRule":"Host(`{{ normalize .Name }}`)","endpoint":"unix:///var/run/docker.sock","network":"proxy","watch":true}
2025-11-15T22:47:13+01:00 INF github.com/traefik/traefik/v3/pkg/provider/aggregator/aggregator.go:219 > Starting provider *acme.Provider
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/aggregator/aggregator.go:220 > *acme.Provider provider configuration config={"HTTPChallengeProvider":{},"ResolverName":"letsencrypt","TLSChallengeProvider":{},"caServer":"https://acme-v02.api.letsencrypt.org/directory","certificatesDuration":2160,"clientResponseHeaderTimeout":"30s","clientTimeout":"2m0s","email":"myemailaddr@gmx.com","keyType":"RSA4096","storage":"/certs/acme.json","store":{},"tlsChallenge":{}}
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:250 > Attempt to renew certificates "720h0m0s" before expiry and check every "24h0m0s" acmeCA=https://acme-v02.api.letsencrypt.org/directory providerName=letsencrypt.acme
2025-11-15T22:47:13+01:00 INF github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:906 > Testing certificate renew... acmeCA=https://acme-v02.api.letsencrypt.org/directory providerName=letsencrypt.acme
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/server/configurationwatcher.go:227 > Configuration received config={"http":{"routers":{"whoami":{"entryPoints":["websecure"],"rule":"Host(`whoami.mydomain.com`)","service":"whoami@file","tls":{"certResolver":"letsencrypt"}}},"services":{"whoami":{"loadBalancer":{"passHostHeader":true,"responseForwarding":{"flushInterval":"100ms"},"servers":[{}],"strategy":"wrr"}}}},"tcp":{},"tls":{},"udp":{}} providerName=file
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/server/configurationwatcher.go:227 > Configuration received config={"http":{"middlewares":{"redirect-web-to-websecure":{"redirectScheme":{"permanent":true,"port":"443","scheme":"https"}}},"routers":{"web-to-websecure":{"entryPoints":["web"],"middlewares":["redirect-web-to-websecure"],"priority":9223372036854775806,"rule":"HostRegexp(`^.+$`)","ruleSyntax":"default","service":"noop@internal"}},"serversTransports":{"default":{"maxIdleConnsPerHost":200}},"services":{"api":{},"dashboard":{},"noop":{}}},"tcp":{"serversTransports":{"default":{"dialKeepAlive":"15s","dialTimeout":"30s"}}},"tls":{},"udp":{}} providerName=internal
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/server/configurationwatcher.go:227 > Configuration received config={"http":{},"tcp":{},"tls":{},"udp":{}} providerName=letsencrypt.acme
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/tls/certificate_store.go:226 > Adding certificate for domain(s) whoami.mydomain.com
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/tls/certificate_store.go:226 > Adding certificate for domain(s) traefik.mydomain.com
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/docker/pdocker.go:85 > Provider connection established with docker 29.0.1 (API 1.52) providerName=docker
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/docker/config.go:200 > Filtering disabled container container=traefik-simpletraefik-55ffeaa5b475a833bd9011e5e112780cdec00923c406de251b5c55e3ddc46e4d providerName=docker
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/docker/config.go:200 > Filtering disabled container container=whoami-simpletraefik-7ea119358ec6b9b6856bbc62bff70ed1cc0c41c8795c26f3827c6cdf4275adf1 providerName=docker
2025-11-15T22:47:13+01:00 DBG github.com/traefik/traefik/v3/pkg/server/configurationwatcher.go:227 > Configuration received config={"http":{},"tcp":{},"tls":{},"udp":{}} providerName=docker
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/tls/tlsmanager.go:386 > No default certificate, fallback to the internal generated certificate tlsStoreName=default
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=SemConvServerMetrics
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=TracingEntryPoint
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/redirect/redirect_scheme.go:29 > Creating middleware entryPointName=web middlewareName=redirect-web-to-websecure@internal middlewareType=RedirectScheme routerName=web-to-websecure@internal
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/redirect/redirect_scheme.go:30 > Setting up redirection to https 443 entryPointName=web middlewareName=redirect-web-to-websecure@internal middlewareType=RedirectScheme routerName=web-to-websecure@internal
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/router.go:37 > Added outgoing tracing middleware entryPointName=web middlewareName=tracing middlewareType=TracingRouter routerName=web-to-websecure@internal serviceName=noop@internal
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=SemConvServerMetrics routerName=web-to-websecure@internal
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=TracingEntryPoint routerName=web-to-websecure@internal
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/recovery/recovery.go:25 > Creating middleware entryPointName=web middlewareName=traefik-internal-recovery middlewareType=Recovery
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=SemConvServerMetrics
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=TracingEntryPoint
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=SemConvServerMetrics
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=TracingEntryPoint
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/server/service/service.go:374 > Creating load-balancer entryPointName=websecure routerName=whoami@file serviceName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/server/service/service.go:432 > Creating server URL= entryPointName=websecure routerName=whoami@file serverIndex=0 serviceName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/service.go:26 > Added outgoing tracing middleware entryPointName=websecure middlewareName=tracing middlewareType=TracingService routerName=whoami@file serviceName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/router.go:37 > Added outgoing tracing middleware entryPointName=websecure middlewareName=tracing middlewareType=TracingRouter routerName=whoami@file serviceName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=SemConvServerMetrics routerName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=TracingEntryPoint routerName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/recovery/recovery.go:25 > Creating middleware entryPointName=websecure middlewareName=traefik-internal-recovery middlewareType=Recovery
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=SemConvServerMetrics
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=TracingEntryPoint
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/server/router/tcp/manager.go:237 > Adding route for whoami.mydomain.com with TLS options default entryPointName=websecure
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:489 > Trying to challenge certificate for domain [whoami.mydomain.com] found in HostSNI rule ACME CA=https://acme-v02.api.letsencrypt.org/directory acmeCA=https://acme-v02.api.letsencrypt.org/directory providerName=letsencrypt.acme routerName=whoami@file rule=Host(`whoami.mydomain.com`)
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:962 > Looking for provided certificate(s) to validate ["whoami.mydomain.com"]... ACME CA=https://acme-v02.api.letsencrypt.org/directory acmeCA=https://acme-v02.api.letsencrypt.org/directory providerName=letsencrypt.acme routerName=whoami@file rule=Host(`whoami.mydomain.com`)
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/tls/certificate_store.go:226 > Adding certificate for domain(s) whoami.mydomain.com
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/tls/certificate_store.go:226 > Adding certificate for domain(s) traefik.mydomain.com
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/tls/tlsmanager.go:386 > No default certificate, fallback to the internal generated certificate tlsStoreName=default
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:1006 > No ACME certificate generation required for domains ACME CA=https://acme-v02.api.letsencrypt.org/directory acmeCA=https://acme-v02.api.letsencrypt.org/directory domains=["whoami.mydomain.com"] providerName=letsencrypt.acme routerName=whoami@file rule=Host(`whoami.mydomain.com`)
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=SemConvServerMetrics
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=TracingEntryPoint
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/redirect/redirect_scheme.go:29 > Creating middleware entryPointName=web middlewareName=redirect-web-to-websecure@internal middlewareType=RedirectScheme routerName=web-to-websecure@internal
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/redirect/redirect_scheme.go:30 > Setting up redirection to https 443 entryPointName=web middlewareName=redirect-web-to-websecure@internal middlewareType=RedirectScheme routerName=web-to-websecure@internal
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/router.go:37 > Added outgoing tracing middleware entryPointName=web middlewareName=tracing middlewareType=TracingRouter routerName=web-to-websecure@internal serviceName=noop@internal
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=SemConvServerMetrics routerName=web-to-websecure@internal
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=TracingEntryPoint routerName=web-to-websecure@internal
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/recovery/recovery.go:25 > Creating middleware entryPointName=web middlewareName=traefik-internal-recovery middlewareType=Recovery
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=SemConvServerMetrics
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=TracingEntryPoint
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=SemConvServerMetrics
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=TracingEntryPoint
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/server/service/service.go:374 > Creating load-balancer entryPointName=websecure routerName=whoami@file serviceName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/server/service/service.go:432 > Creating server URL= entryPointName=websecure routerName=whoami@file serverIndex=0 serviceName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/service.go:26 > Added outgoing tracing middleware entryPointName=websecure middlewareName=tracing middlewareType=TracingService routerName=whoami@file serviceName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/router.go:37 > Added outgoing tracing middleware entryPointName=websecure middlewareName=tracing middlewareType=TracingRouter routerName=whoami@file serviceName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=SemConvServerMetrics routerName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=websecure middlewareName=tracing middlewareType=TracingEntryPoint routerName=whoami@file
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/recovery/recovery.go:25 > Creating middleware entryPointName=websecure middlewareName=traefik-internal-recovery middlewareType=Recovery
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/semconv.go:40 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=SemConvServerMetrics
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/middlewares/observability/entrypoint.go:37 > Creating middleware entryPointName=web middlewareName=tracing middlewareType=TracingEntryPoint
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/server/router/tcp/manager.go:237 > Adding route for whoami.mydomain.com with TLS options default entryPointName=websecure
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:489 > Trying to challenge certificate for domain [whoami.mydomain.com] found in HostSNI rule ACME CA=https://acme-v02.api.letsencrypt.org/directory acmeCA=https://acme-v02.api.letsencrypt.org/directory providerName=letsencrypt.acme routerName=whoami@file rule=Host(`whoami.mydomain.com`)
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:962 > Looking for provided certificate(s) to validate ["whoami.mydomain.com"]... ACME CA=https://acme-v02.api.letsencrypt.org/directory acmeCA=https://acme-v02.api.letsencrypt.org/directory providerName=letsencrypt.acme routerName=whoami@file rule=Host(`whoami.mydomain.com`)
2025-11-15T22:47:14+01:00 DBG github.com/traefik/traefik/v3/pkg/provider/acme/provider.go:1006 > No ACME certificate generation required for domains ACME CA=https://acme-v02.api.letsencrypt.org/directory acmeCA=https://acme-v02.api.letsencrypt.org/directory domains=["whoami.mydomain.com"] providerName=letsencrypt.acme routerName=whoami@file rule=Host(`whoami.mydomain.com`)
2025-11-15T22:47:30+01:00 DBG github.com/traefik/traefik/v3/pkg/server/service/loadbalancer/wrr/wrr.go:176 > Service selected by WRR:
2025-11-15T22:47:30+01:00 DBG github.com/traefik/traefik/v3/pkg/proxy/httputil/proxy.go:121 > 500 Internal Server Error error="unsupported protocol scheme \"\""
2025-11-15T22:47:33+01:00 DBG github.com/traefik/traefik/v3/pkg/server/service/loadbalancer/wrr/wrr.go:176 > Service selected by WRR:
2025-11-15T22:47:33+01:00 DBG github.com/traefik/traefik/v3/pkg/proxy/httputil/proxy.go:121 > 500 Internal Server Error error="unsupported protocol scheme \"\""
2025-11-15T22:47:53+01:00 DBG github.com/traefik/traefik/v3/pkg/server/service/loadbalancer/wrr/wrr.go:176 > Service selected by WRR:
2025-11-15T22:47:53+01:00 DBG github.com/traefik/traefik/v3/pkg/proxy/httputil/proxy.go:121 > 500 Internal Server Error error="unsupported protocol scheme \"\""
Thanks a lot in advance!!